HTTP
In most cases, whatever we build involves some sort of internet connection. The language that is used to communicate over the internet is called Hyper Text Transfer Protocol (HTTP). It is the set of rules that govern how two devices should communicate with each other over the internet. It functions mainly as a request-response cycle between a client and a server. A client makes a request and a server responds. Web browsers such as Chrome or Safari, the Facebook app on your mobile or a weather app on your desktop are clients. A server can be a web server like Apache, or Nginx or a Java-enabled web server like Tomcat. API calls also use the HTTP protocol to send requests and get responses.
In the OSI model, HTTP is a layer 7 protocol.
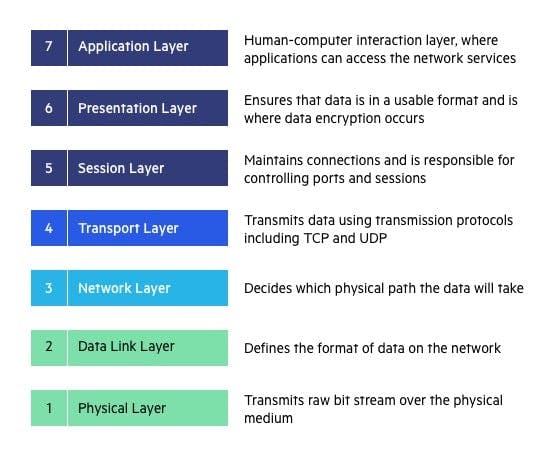
What is an HTTP request? What is an HTTP response?
HTTP requests are generated by a user's browser as the user interacts with web properties. For example, if a user clicks on a hyperlink, the browser will send a series of HTTP GET requests for the content that appears on that page.
These HTTP requests all go to a server, and that server generates an HTTP response. HTTP responses are answers to HTTP requests.
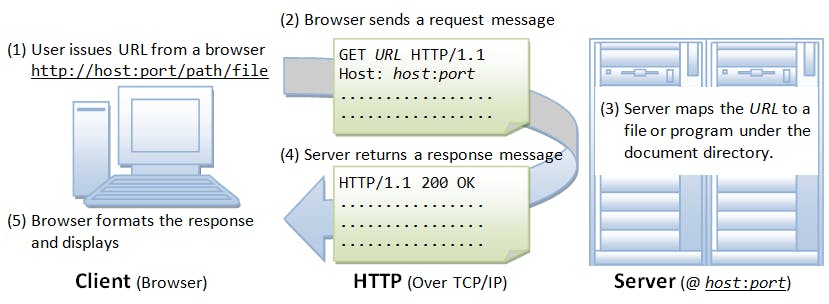
HTTP vs HTTPS
HTTPS is HTTP with encryption and verification. The only difference between the two protocols is that HTTPS encrypts normal HTTP requests and responses and digitally signs them. As a result, HTTPS is far more secure than HTTP. A website that uses HTTP has http:// in its URL, while a website that uses HTTPS has https://.
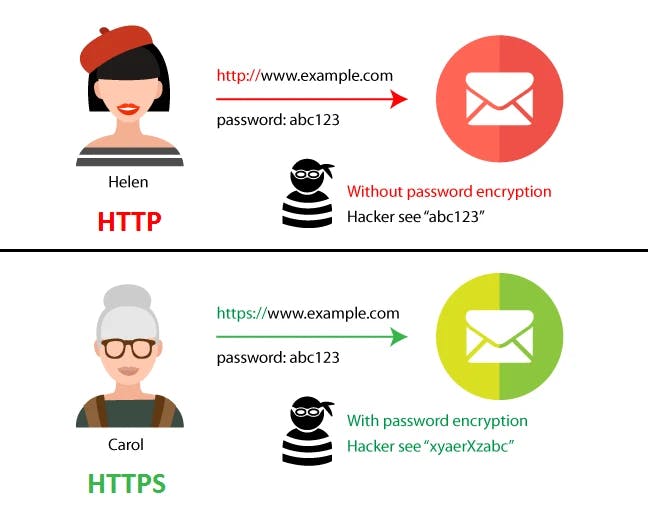
What is encryption?
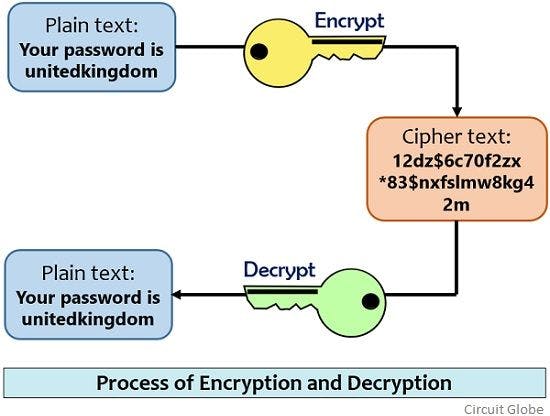
Encryption takes readable data and alters it so that it appears random. Encryption requires the use of a cryptographic key: a set of mathematical values that both the sender and the recipient of an encrypted message agree on.
Although encrypted data appears random, encryption proceeds in a logical, predictable way. Truly secure encryption will use keys complex enough that a third party is highly unlikely to break by guessing the key.
What is authentication
Authentication means verifying that a person or machine is who they claim to be. In HTTP, there is no verification of identity. But on the modern Internet, authentication is essential. Just like an ID card confirms a person's identity, a private key confirms the server's identity. This provides confirmation that the server is who it claims to be.
Migrating APIs to HTTPS
What are APIs?
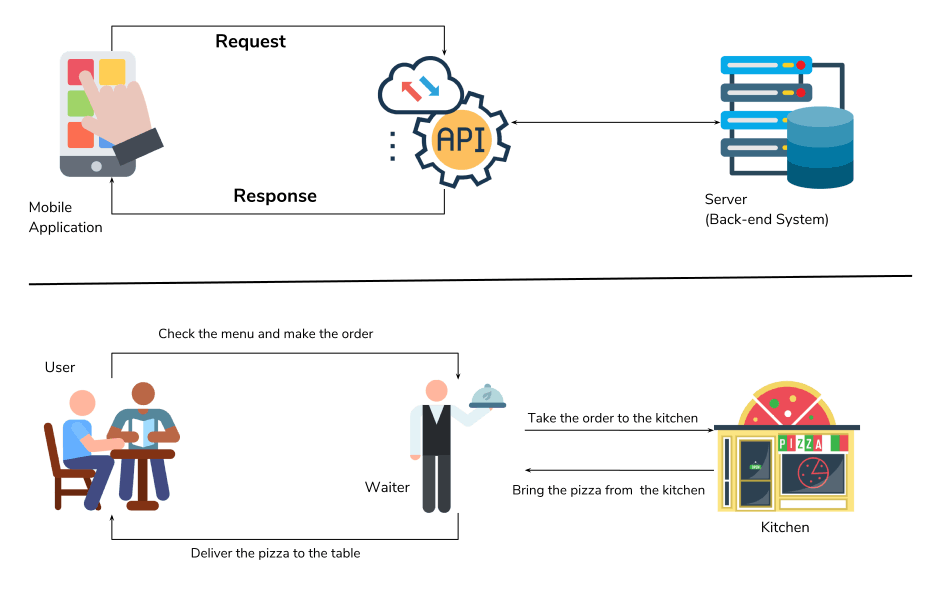
API stands for Application Programming Interface. In the context of APIs, the word Application refers to any software with a distinct function. The interface can be thought of as a contract of service between two applications. This contract defines how the two communicate with each other using requests and responses. Their API documentation contains information on how developers are to structure those requests and responses.
Why should we migrate APIs to HTTPS?
All APIs should use and require HTTPS to help guarantee confidentiality, authenticity, and integrity.
Confidentiality: The visitor’s connection is encrypted, obscuring URLs, cookies, and other sensitive metadata.
Authenticity: The visitor is talking to the “real” website, and not to an impersonator or through a person in the middle.
Integrity: The data sent between the visitor and the website has not been tampered with or modified.
A plain HTTP connection can be easily monitored, modified, and impersonated.
HTTPS encrypts nearly all information sent between a client and a web service.
For example, an unencrypted HTTP request reveals not just the body of the request, but the full URL, query string, and various HTTP headers about the client and request:
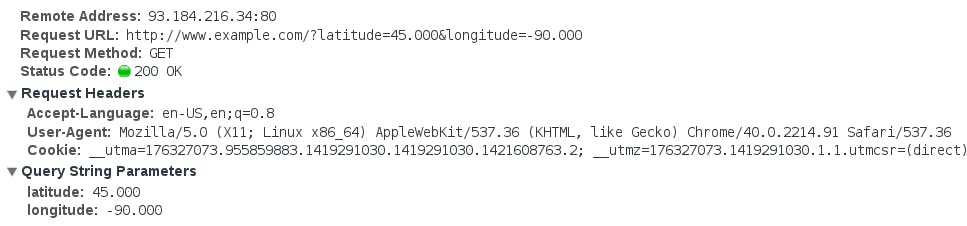
An encrypted HTTPS request protects most things:

This is the same for all HTTP methods (GET, POST, PUT, etc.). The URL path and query string parameters are encrypted, as are POST bodies.
What information does HTTPS not protect? HTTPS encrypts the entire HTTP request and response. But the DNS resolution and connection setup can reveal other information, such as the full domain or subdomain and the originating IP address. Attackers can still analyze encrypted HTTPS traffic for “side channel” information like the time spent on site or the relative size of user input.
HTTPS provides a stronger guarantee that a client is communicating with the real API and receiving back authentic content. It also enhances privacy for applications and users using the API.
